Table of Contents
The netstat command is a powerful tool for diagnosing network issues, checking open ports, and viewing active connections on both Linux and Windows systems. In this guide, we’ll explore seven practical ways to use netstat, including examples on Linux distributions like Ubuntu and Debian, and how to troubleshoot common issues like “netstat command not found.”
What is the netstat command?
The netstat (network statistics) command displays information about network connections, routing tables, interface statistics, masquerade connections, and multicast memberships. It is widely used by system administrators and developers to manage network configurations and analyze traffic or port-related issues.
1. List All Open Network Connections
To show all active connections (TCP and UDP), use:
netstat -a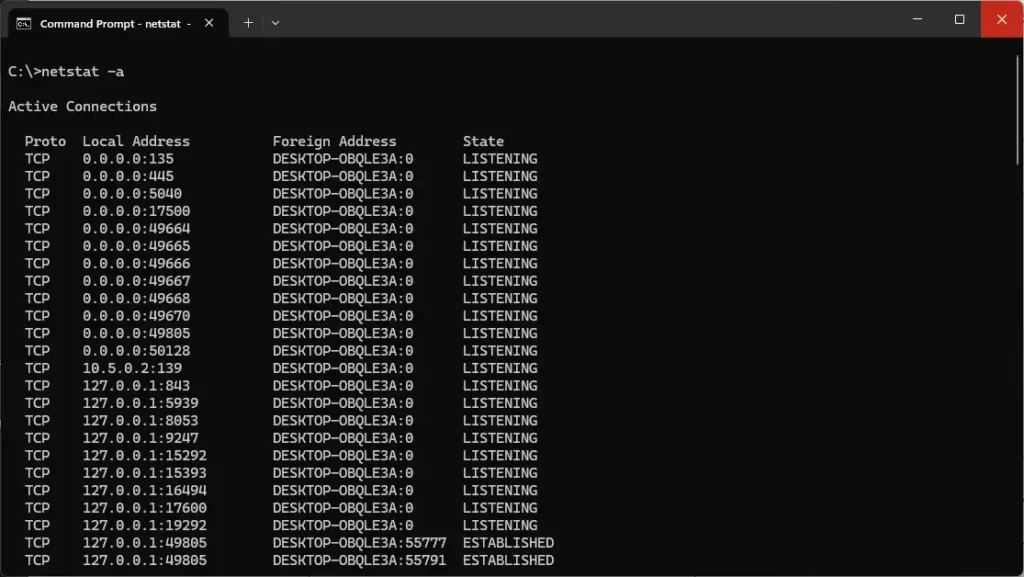
This lists all ports your machine is listening to, and all established connections using any protocol.
| Flag | Description |
|---|---|
| -a | Displays all connections and listening ports |
| -t | Show only TCP connections |
| -u | Show only UDP connections |
| -l | Show only listening sockets |
| -p | Displays the process using the port |
| -n | Show numerical addresses instead of resolving hosts |
2. Use netstat to Check Listening Ports
To see ports that are being listened to (especially useful for troubleshooting server configurations):
netstat -tulnThis will display TCP (-t) and UDP (-u) ports in a numeric format (-n), showing only listening ports (-l).
This output is helpful to discover which servers (like Apache, MySQL, Nginx) are running and listening on which ports.
3. Monitor Specific Ports
If you want to scan for a specific port (e.g., port 80), you can combine netstat with grep on Linux:
netstat -tuln | grep :80This helps when you’re trying to ensure that a web server or custom application is up and reachable.
4. netstat to Identify Listening Programs (netstat tulpn)
To see which processes (with process IDs) are listening on various ports, use:
netstat -tulpnThis is especially helpful for security monitoring or debugging “port already in use” errors.
5. Install netstat on Ubuntu and Debian
If the netstat command is not found, it likely means net-tools is not installed.
sudo apt update
sudo apt install net-toolsThis works for both Ubuntu and Debian systems.
6. How to Kill a Process Using a Port in Windows
If a port is blocked by a hung process, you can kill a port in Windows by finding and stopping the process:
- Run
netstat -ano | findstr :PORT. - Note the PID (Process ID).
- Run
taskkill /PID <PID> /Fto forcibly stop it.
This is the fastest way to kill a process on a port in Windows.
7. View All Open Ports on Windows
To see all ports your Windows system is listening on, use:
netstat -an | find "LISTENING"Want more detail? Combine it with tasklist to match PIDs to process names.
This is used in system hardening and security audits to view windows netstat listening ports and eliminate potential backdoors.
Bonus: Replacing netstat with ss
On many modern Linux distributions, ss is the preferred alternative. It is faster and more informative:
ss -tulpnss stands for “socket statistics” and can give deeper insights than netstat.
When netstat command is not found
If you see “netstat: command not found“, install the package:
- For Ubuntu/Debian:
sudo apt install net-tools - For RHEL/CentOS:
sudo yum install net-tools
Wrapping up
The netstat command is still a vital tool in 2024 for diagnosing network issues, analyzing open ports, and tracking down rogue processes. Whether you’re using Linux or Windows, mastering netstat and its many options will improve your network troubleshooting effectiveness significantly.
External Resources
Frequently Asked Questions (FAQ)
- Q: How do I install netstat on Ubuntu or Debian?
A: Runsudo apt install net-tools. - Q: What does netstat tulpn do?
A: It shows TCP/UDP ports in listening state along with the PID and program name. - Q: How do I check if a port is open in Windows?
A: Usenetstat -an | findstr LISTENINGor tools liketelnet. - Q: How to kill process using specific port in Windows?
A: Find PID withnetstat -ano, then usetaskkill /PID <PID> /F. - Q: What’s the difference between netstat and ss?
A: ss is faster and more modern, but netstat remains widely used and familiar.
Related Resources:
- Learn how to resolve domain names to IP addresses: 7 Powerful Uses of the nslookup Command in Windows (Explained)
- Master path tracing techniques: Traceroute Command Guide