DNS in networking is the system that allows users to access websites using human-readable names instead of numeric IP addresses. This guide is written for students, beginner network engineers, IT professionals, and anyone curious about how the internet works behind the scenes. If you have ever wondered how typing a domain name instantly loads a website, this article walks you through that process step by step.
You will learn how domain names are translated into IP addresses, how the DNS hierarchy is structured, and what roles recursive and authoritative servers play. The guide also explains DNS records, caching, and key security mechanisms such as DNSSEC.
By the end, you will understand not only what DNS does, but also how it works internally and why it plays such a central role in modern networking.
Table of Contents
What Is DNS in Networking and Why It Matters
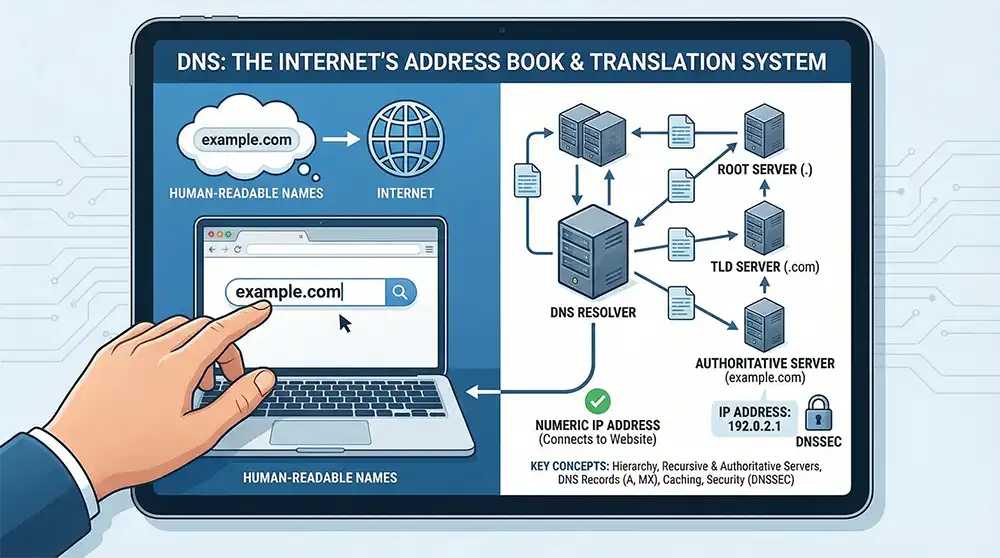
The Domain Name System (DNS) is a hierarchical and distributed naming system. This section defines the core concept clearly and simply. Often called the “phonebook of the internet,” it converts human-friendly names into machine-readable IP addresses so devices can communicate.
Without this system, users would have to remember numeric addresses for every website they visit. Instead, DNS servers handle the translation automatically, making the internet practical and scalable.
- It translates domain names into IP addresses.
- It distributes data across multiple global servers.
- It enables scalable and reliable name resolution.
How DNS translates domain names into IP addresses
When you type a web address into your browser, DNS servers start a lookup process. Computers communicate using IP addresses, which are numeric identifiers assigned to each device on a network. Because numbers are difficult to remember, DNS bridges the gap between domain names and those numeric values.
The result is seamless browsing. The correct IP address is returned, and your browser connects to the appropriate server.
The DNS Hierarchy and How Resolution Works
DNS was designed as a hierarchical, distributed database. To understand how it functions at scale, you need to look at its structure. This design ensures that no single server stores all domain data, which supports reliability and scalability.
DNS resolution follows a top-down path through several layers, each responsible for a specific part of the lookup process.
Root, TLD, and authoritative servers in the DNS hierarchy
The DNS hierarchy consists of root servers, top-level domain (TLD) servers, and authoritative servers. There are 13 root nameserver identities at the top of the system. They direct queries to the correct TLD servers, such as those responsible for .com or .org.
TLD servers then forward the request to the appropriate authoritative servers. Authoritative servers provide the final answer by returning the IP address associated with the requested domain.
This layered approach allows the system to support large numbers of registered domains efficiently.
Types of DNS Servers in Networking
DNS architectures consist of two types of DNS servers: recursive servers and authoritative servers. After reviewing the hierarchy, it helps to focus on the specific server roles within it. Each type performs a distinct but complementary function.
Understanding this distinction is helpful for troubleshooting and designing resilient network infrastructures.
Recursive DNS resolvers and DNS caching
An initial query from a client device is sent to a recursive DNS resolver. The resolver acts as an intermediary, contacting root, TLD, and authoritative servers on behalf of the client. Users typically do not query authoritative servers directly.
Recursive DNS services improve performance through DNS caching. When a resolver receives a response, it stores it temporarily based on the Time-to-Live value. This reduces repeated queries and speeds up future lookups.
Authoritative DNS and final answers for a domain
Authoritative DNS has the final authority over a domain. These servers store official DNS records and respond with definitive answers to queries. They do not typically perform recursive lookups.
The data they manage is organized in zone files, which contain resource records such as A and NS records. This makes authoritative servers the trusted source for domain configuration.
| Server Type | Main Function | Caching Behavior |
|---|---|---|
| Recursive resolver | Queries other DNS servers and returns results to clients | Caches results based on TTL to improve performance |
| Authoritative server | Provides final answer for a domain using stored DNS records | Does not rely on cached third-party results for authority |
DNS Records and IP Address Mapping
An A record maps a domain name to an IPv4 address. With the server roles clarified, the next step is to examine the records they manage. These records define how a domain behaves and where its traffic is directed.
Each record type serves a specific purpose in connecting names to network resources.
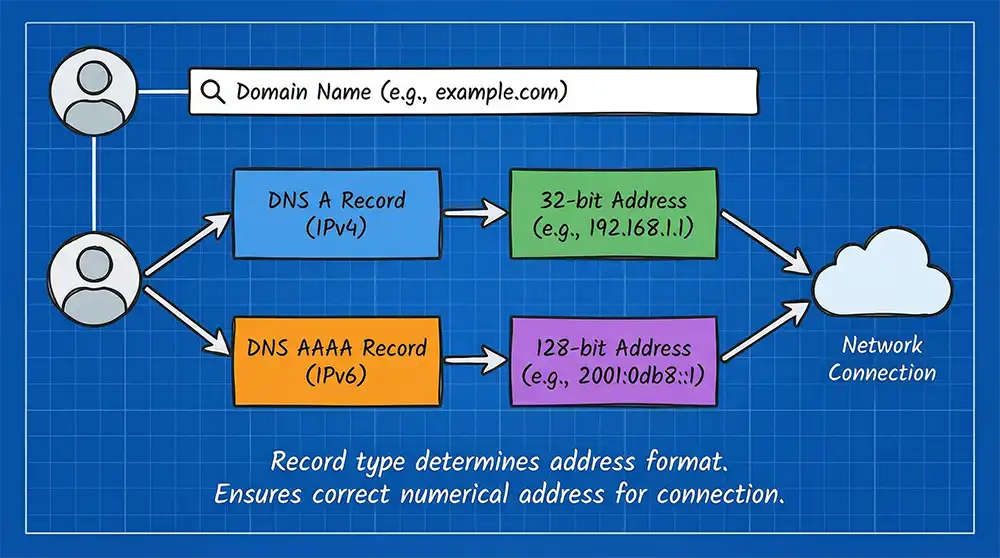
A records, IPv4, and IPv6 addressing
An A record links a domain to an IPv4 address, which uses 32-bit numbers. For newer networks, AAAA records map domains to IPv6 addresses, which use 128-bit numbers. The record type determines which address format is returned.
These DNS records ensure that when a user enters a domain, the correct numerical address is returned for the connection.
DNS zone files and mandatory records
DNS zone files are text-based files that store resource records for a domain. They typically begin with mandatory records such as the NS record, which identifies authoritative name servers.
Zone files may also include A, AAAA, MX, and other record types. Together, these entries determine how a domain routes traffic and supports services like email.
- Explain how domain names map to IP addresses
- Describe recursive and authoritative server roles
- Summarize caching and DNSSEC protection
DNS Security and Common Threats
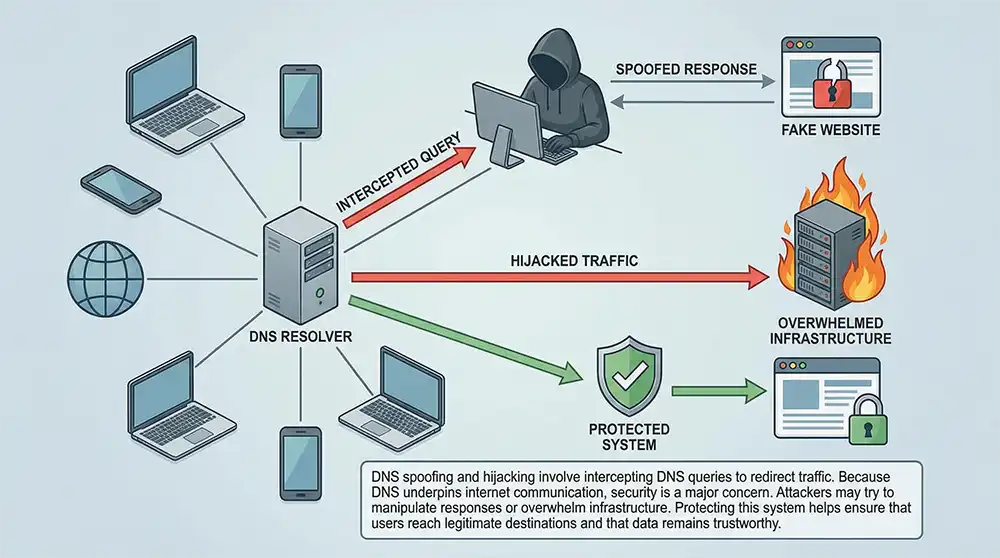
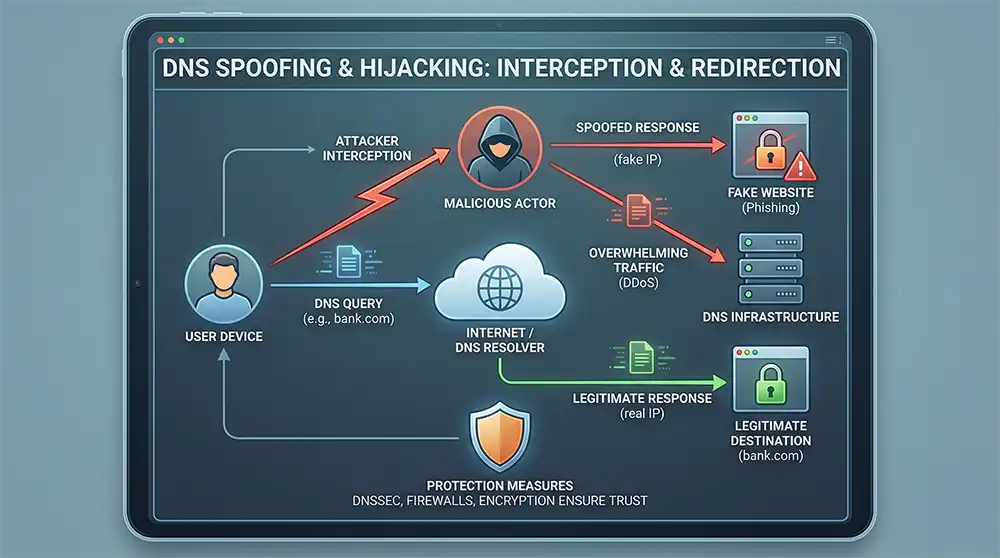
DNS spoofing and hijacking involve intercepting DNS queries to redirect traffic. Because DNS underpins internet communication, security is a major concern. Attackers may try to manipulate responses or overwhelm infrastructure.
Protecting this system helps ensure that users reach legitimate destinations and that data remains trustworthy.
DNSSEC and authentication of DNS records
DNSSEC adds cryptographic signatures to DNS records. These signatures provide authentication, allowing resolvers to verify that responses have not been altered in transit.
By validating digital signatures, DNSSEC increases trust in DNS responses and reduces the risk of cache poisoning or tampering.
DNS attacks and DNS hijacking trends
DNS infrastructure is frequently targeted. Industry surveys indicate that many organizations report experiencing DNS attacks, and DNS hijacking is considered a major challenge.
While survey figures vary, they show why monitoring, redundancy, and security extensions play an important role.
Common Mistakes and Myths About DNS in Networking
DNS matches website names to IP addresses. After reviewing how it works and the risks involved, it helps to clear up common misconceptions. Several myths persist, especially among beginners.
Addressing these misunderstandings strengthens foundational networking knowledge.
Myth: DNS and DHCP are the same service
DNS and DHCP perform different roles. DNS resolves names to IP addresses, while DHCP handles IP address assignment and network configuration for devices.
Although they often work together in enterprise networks, they remain separate services with distinct purposes.
Myth: DNS cannot scale to millions of registered domains
There are currently more than 342 million registered domains. The distributed system design and DNS hierarchy make this scale possible.
Because responsibility is divided among root, TLD, and authoritative servers, the system can expand without creating central bottlenecks.
Frequently Asked Questions
What is DNS in networking?
It is a hierarchical and distributed system that translates domain names into IP addresses. Its core purpose is to make internet resources accessible using human-readable names instead of numbers.
What are the main types of DNS servers?
The two main types are recursive and authoritative servers. Recursive servers query others on behalf of clients, while authoritative servers provide final answers for domains they manage.
How does DNS caching improve performance?
Recursive resolvers store recent lookup results temporarily. This reduces repeated external queries and speeds up future access to the same domain.
What is DNSSEC used for?
DNSSEC is used to authenticate DNS records with cryptographic signatures. It helps prevent tampering and ensures responses are trustworthy.
How many root DNS servers exist?
There are 13 root nameserver identities at the top of the DNS hierarchy. They direct queries to the appropriate TLD servers during resolution.
Key Takeaways
DNS translates domain names into IP addresses using a hierarchical and distributed structure. Queries move from recursive resolvers through root and TLD servers to authoritative servers.
Recursive servers handle lookups and DNS caching, while authoritative servers provide final answers based on stored DNS records. Security mechanisms such as DNSSEC add authentication and protect against tampering.
Relevant Internal Links
- What is a DNS?
- Most Popular Domain Registrars
- How to Find DNS Provider
- DNS Record Types You Must Know